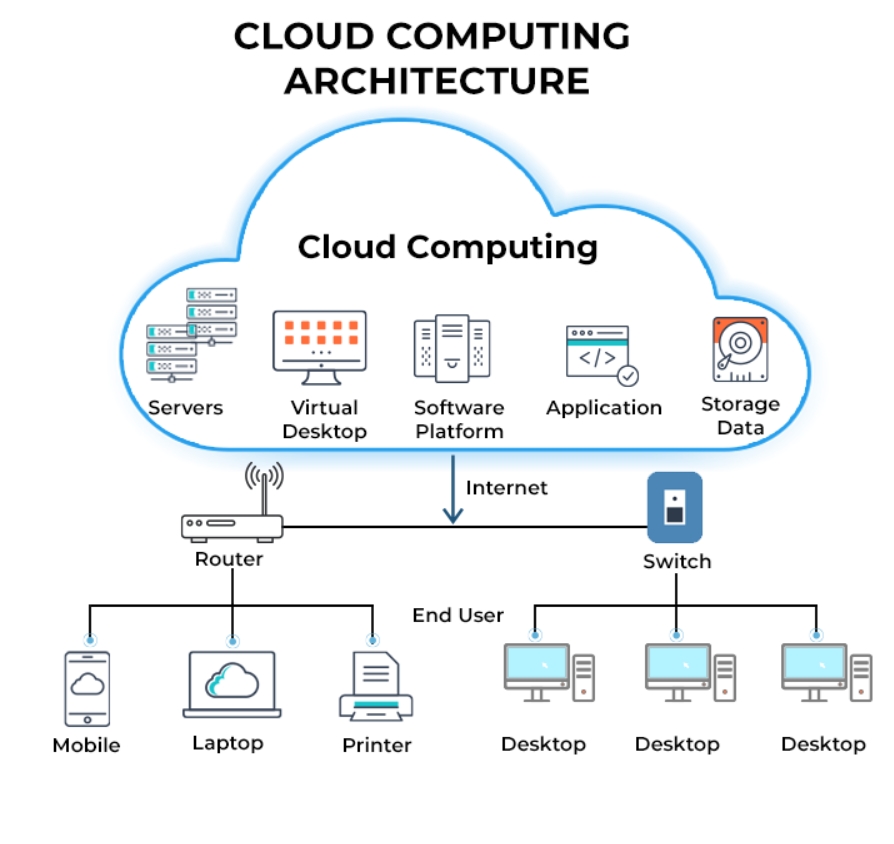
AI Program Management
Strategic Planning, Governance & Compliance, Technology & Infrastructure, Cross-Functional Collaboration, Risk Management, Performance Monitoring:

Stakeholder Vision
Internal: Executives & Leadership, Project Managers, Developers & Engineers, Marketing & Sales Teams, UI/UX, L1 , L2, L3, L4 Engineers, Scrum Master, Blockchain innovators

DevOps
Collaboration & Automation, Continuous Integration (CI), Continuous Deployment (CD), Infrastructure as Code (IaC), Monitoring & Logging, Security (DevSecOps)

Cloud Modernization
Focus on Cloud Migration, AI/ML integration, and Enterprise Digital Transformation.

Banking Crypto ISO
CryptoISO, ISO CryptoX, CryptoISO Nexus, ISOChain, MetaISO

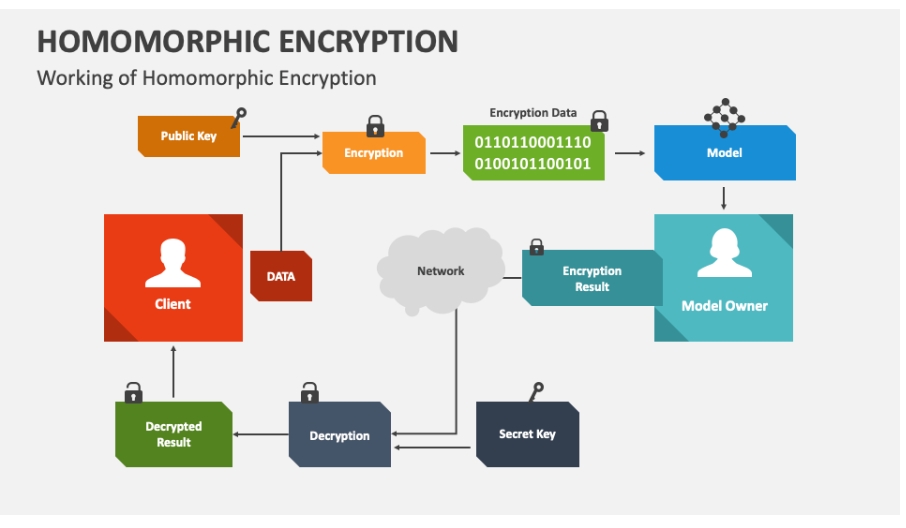
Cryptography
Symmetric Encryption, Asymmetric Encryption, Hashing, Digital Signatures

NFT Digital Art
Each NFT has a unique digital signature recorded on the blockchain, Ownership & Provenance, Interoperability, Smart Contracts & Royalties

Globalization AI / ML
AI for Business Automation, ML for Cloud Modernization, Global AI Expansion,

Blockchain
Decentralization, Transparency, Immutability, Security, Smart Contracts,

Beautiful minds of innovation design is incoming.
Working on a new design of technology can be very challenging and mind-boggling at the same time. GRIT will be the personality trait and ability to persevere and stay passionate about the long-term goals. Stay the course and never ever give up. Be Strongly Persistence!
Empowering your digital marketing strategy with AI /ML
1. Define Your Goals: Before diving into the vast ocean of digital marketing, it’s crucial to define your goals. …
2. Know Your Audience:
3. Optimize Your Website for SEO:
4. Create Compelling Content:
5. Utilize Social Media Effectively:
6. Implement Email Marketing Campaigns:
7. Invest in Paid Advertising:
8. Monitor Analytics and Adjust Accordingly:
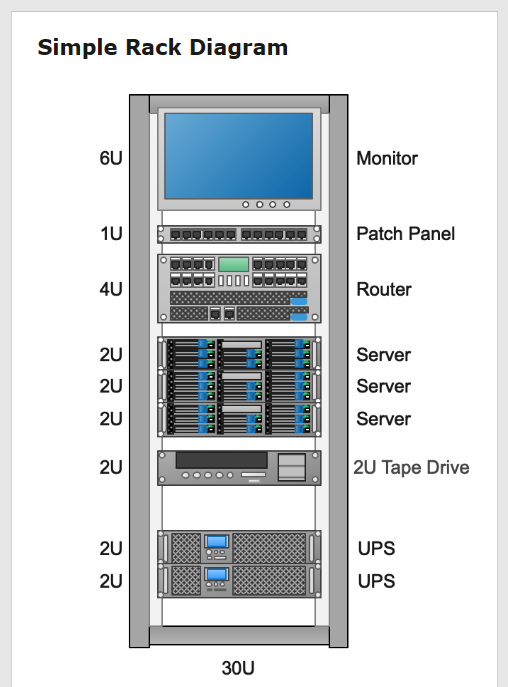
Take your brand to next Infrastructure Network Engineering design / White Space innovation.
Servers, Network switches, Routers, Patch panels, Cables, Cable management bars, Blanking panels, Power distribution units (PDUs), Mounting rails,
LAN & WAN Network
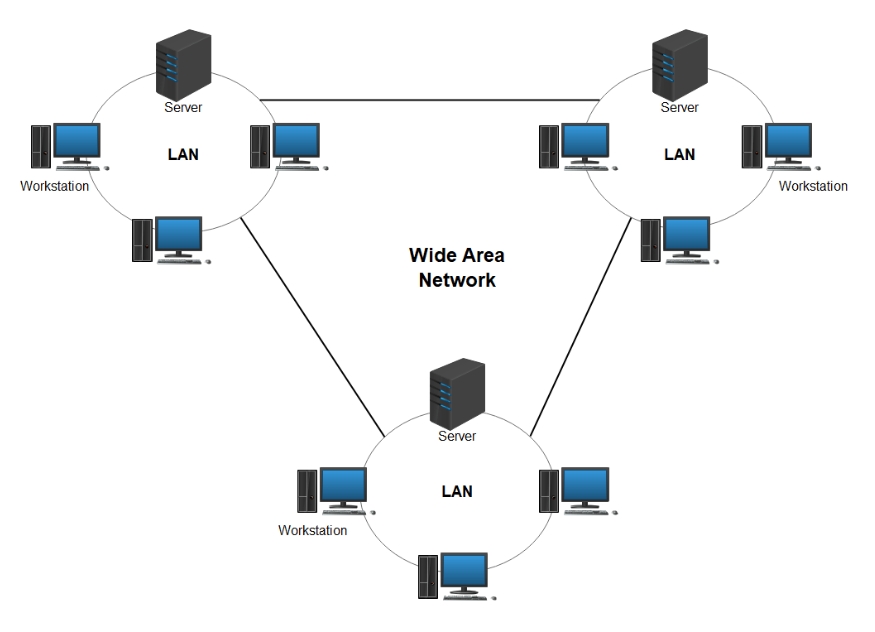
Local Area Network

Corporate IT Office

Building a partnership with investors and believers!
Checkout our area of expertise. Current trends
Cybersecurity, Cloud Computing, Artificial Intelligence (AI) Software Development, DevOps, Web Developer, Mobile Application Developer, IT Security Specialist, Video Game Designer, Network Administrator, Database Administrator,
Technology Manager
Technology Manager Employment Projections | 2022 – 2032
10-Year Growth Pct: 15% (much faster than avg.)†
10-Year Growth Volume: 86,000 new jobs
AI Program Manager
Technology Manager Employment Projections | 2022 – 2032
10-Year Growth Pct: 20% (much faster than avg.)†
10-Year Growth Volume: 96,000 new jobs
Initiation
Build a contract for deployment and completing the accurate research could be very difficult .
Develop a business case
Identify scope – Infra. Risk, Vendor, Budget
Identify project stake-holders
Planning
Develop a business case,
Project Plan – workflow document
Gather team documents
Estimate budget
Kick off team meeting to include, Leadership, Vendors, External and Internal teams to discuss scope of project and milestone date. Roadmap Diagram is essential with Phases

Execution
Monitor team advancement toward completion of project goals
Brief team on task and project scope
Monitor quality of work.
Estimate budget
Manager budget
Project Milestone Date
Closing out all tasks and project responsibilities for final cut-over.
Analyze project and team results
Document project closure
Account used and unused budget
Project Sign off
Leadership, External Vendor and Internal will sign off about project completion
Cloud, IaaS, SaaS, PaaS

 5 Days N. Office/ Hybrid/ Remote $ Let’s Go to Work!!
5 Days N. Office/ Hybrid/ Remote $ Let’s Go to Work!!